- The concerns surrounding the coronavirus outbreak are being exploited by hackers taking advantage of people’s thirst for information.
- An Android app called “COVID19 Tracker” is just one example of ransomware that masks itself as a real-time coronavirus map tracker, according to researchers.
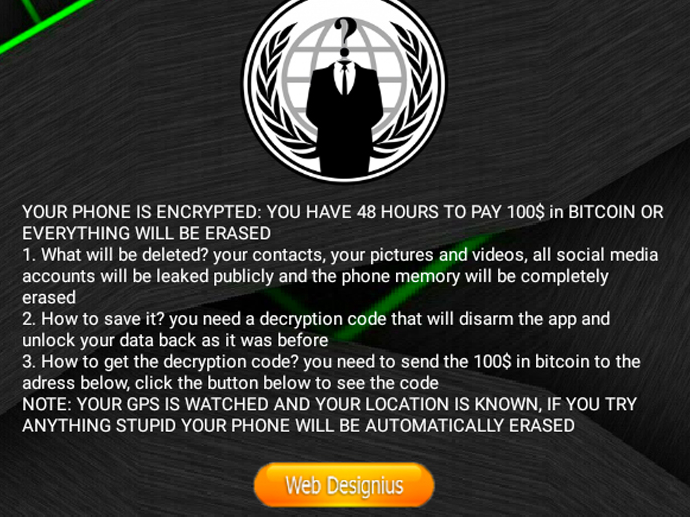
- If a user grants the app access to certain phone settings, the ransomware is enabled and locks the user ouf of their phone unless they pay $100 in bitcoin to the hackers within 48 hours.
- If the victim doesn’t comply, the ransomware threatens to delete their phone’s storage and leak social media accounts.
- The website that hosts the ransomware app still appears active. The app isn’t found on the Google Play Store, where the risk of downloading malware is significantly lower.
- Visit Business Insider’s homepage for more stories.
Unsurprisingly, people are turning to the internet to get up-to-the-minute information on the coronavirus outbreak, but the thirst for information during a pandemic is a perfect opportunity for hackers. It’s also a good time to remind everyone that hackers are still hard at work, even during concerning times.
An app called “COVID19 Tracker” masking itself as a coronavirus outbreak map tracker is actually ransomware that locks down your phone and demands you pay the hackers $100 in bitcoin within 48 hours, according to Chad Anderson and Tarik Salehat at internet security company DomainTools.
Saleh’s report from Friday shows that the app is designed for the Android operating system, and was listed to Android users searching the web for coronavirus tracking apps. To download the app, a user would have to go directly to the website where the app was hosted and download the app from there. The app was not available on the Google Play Store, according to Saleh.
The website appears to have been taken down as of Monday afternoon, but it was still running on Monday morning. The site prompts visitors to download an app, saying, “for android users: to get real-time number of coronavirus cases based on your GPS location please download the mobile app version of the website and enable ‘accurate reporting’ for best experience.” Business Insider isn’t linking or posting the name of the site.
Once opened, the app asks for access to your lock screen to give you "instant alerts when a coronavirus patient is near you." The app also asks for permission of an Android phone's accessibility settings for "active state monitoring."
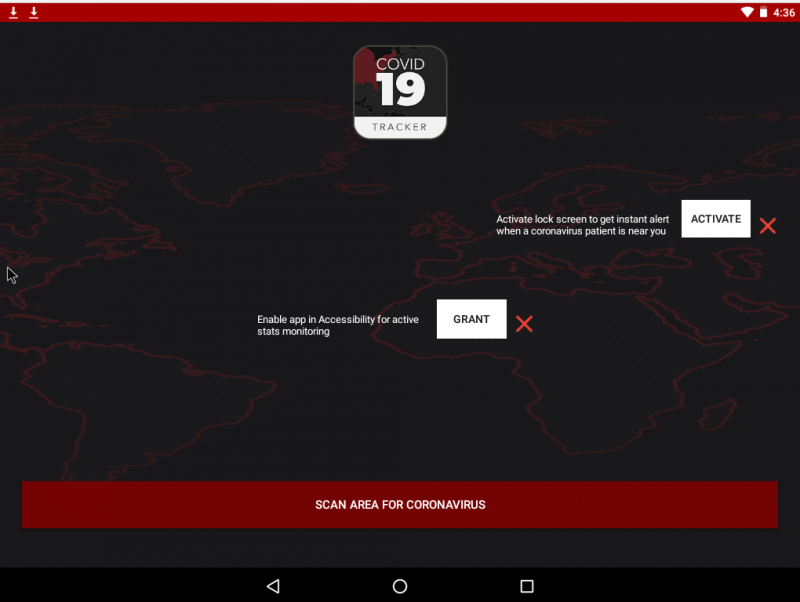
If an unsuspecting user grants these permissions to the app, ransomware dubbed "CovidLock" is enabled, and the screen changes to a ransom note, shown below:
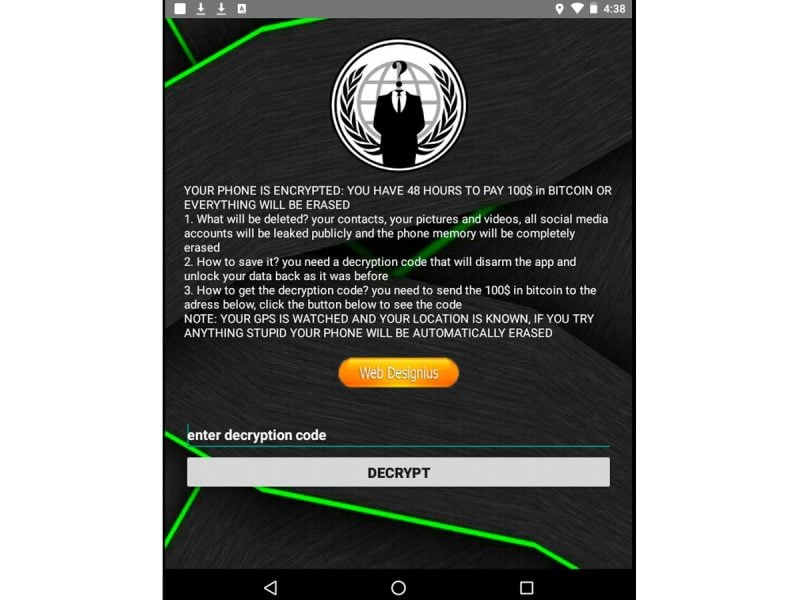
The note says:
"Your phone is encrypted: You have 48 hours to pay 100$ [sic] in bitcoin or everything will be erased. 1. What will be deleted? your contacts, your pictures and videos, all social media accounts will be leaked publicly and the phone memory will be completely erased 2. How to save it? you need a decryption code that will disarm the app and unlock your data back as it was before 3. How to get the decryption code? you need to send 100$ [sic] in bitcoin to the adress [sic] below, click the button below to see the code Note: Your GPS is watched and your location is known, if you try anything stupid your phone will be automatically erased"
At the end of the note is a text field where a victim is meant to enter the decryption code, and a button beneath the text field that says "Decrypt."
Saleh notes that protections against this kind of attack in the Android operating system have been in place since Android 7 "Nougat" released in 2016, just as long as the user has set a password to unlock the phone. Without an unlocking password, users are still vulnerable to attacks like the CovidLock ransomware.
Saleh said that the DomainTools security research team had reverse engineered the decryption key, and has released it publicly here so that victims could unlock their devices without paying the ransom.
When asked whether the hackers could simply generate a new decryption key, DomainTools told Business Insider that the hackers would need to rewrite the malware and redeploy it, and a new key wouldn't affect anyone who has already downloaded the infected app. "That is one of the big flaws of CovidLock," DomainTools said.
The company is also monitoring the hackers' bitcoin wallet and its activity, and DomainTools told Business Insider that no one has paid the ransom to the hackers as of yet, but the company is unsure of how many people have downloaded the app.
DomainTools advises that people obtain information regarding COVID-19 from trusted sources like government and research institutions. It also suggests that people don't open emails or click links with health-related content, as miscreants are "trying to capitalize on fear." And finally, it advises Android users to download apps exlusively from the Google Play Store, where there is less risk of downloading malware.
This isn't the first instance of malware apps masking themselves as coronavirus-related tracking apps. Last week, cybersecurity researchers identified several fake COVID-19 tracker maps that infect people's computers with malware when opened.